Dehashed Alternatives -Dehashed is a cutting-edge fraud and security tool that enables the retrieval of information from corrupted databases.
You can use the website Dehashed to see if your personal data has been stolen or leaked.
In other words, Dehashed alternatives is a search engine for security analysts, reverse engineers, and computer hackers.
According to its statement, DeHashed is the largest & fastest data breach search engine.
You can search for usernames, emails, passwords, addresses, and phone numbers using the browser software.
Users can submit their own software or unprocessed data to the website through the use of the API.
Because of the user-friendly interface, users can easily locate their leaked information.
It also provides a free service for finding hashes and accessing publicly available data, however it does charge money for database access.
Features:
It shows how many times the file has been shared on different web platforms using the SHA-256 hash of the file. Before doing this you must register and also it’s free.
Dehashed collects the most recent hashes in numerical order and analyzes them. Additionally, the website provides filters for particular hash types, such as Steam trade URLs.
With the help of the autocomplete tool, you can easily locate hashes by using the filters on their search phrases.
Let us have a look at the Dehashed Alternatives:
#1 LeakCheck
LeakCheck is a secure platform that enables you to save the digital identities of individuals and companies.
The platform lets you save login information for developers’ access to APIs for any subscription.
Also, this platform is useful for businesses and developers since it allows them to store their information and safeguard those of users accessing their apps, websites, etc.
By logging in, domain, password, hash, or keyword, LeakCheck lets you do searches.
The platform offers you an advanced solution that secures your data for around two years.
Additionally, users may perform large searches, which is quite useful, especially for businesses with a large workforce.
This is one of the best Dehashed Alternatives.
#2 Snusbase
Snusbase is a reliable data search tool that enables you to keep up with the most recent database hacks.
The tool offers information about the files that have been stolen from your website and internet security.
Also, it enables you to look for personal data such as hashes, emails, usernames, and passwords.
This platform differs from others, such as DeHashed, in that it provides users with more focused search results. Their databases, however, are not as big as DeHashed’s.
Furthermore, the app offers users an opportunity to regain control over hacked accounts and data.
#3 Nuclear Leaks
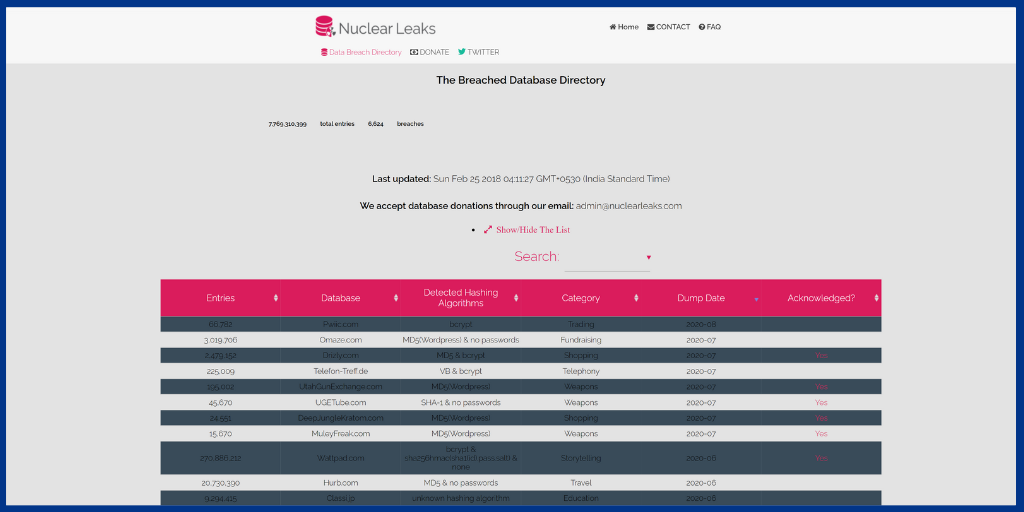
NuclearLeaks is an advanced platform that provides a huge collection of databases from websites that are accessible to the general public.
Mostly, users who commonly utilize this platform are journalists and security experts.
Nuclear Leaks is a tool for monitoring any potential hazards to your information as well as a search engine for data leaks.
It also aims to educate users about database hacks by offering information about published data.
Users are able to search a database of leaked data for data such as addresses, emails, usernames, or phone numbers.
And also the number of entries, hashing formulas, categories, and the dump date are all provided by NuclearLeaks.
#4 FireFox Monitor
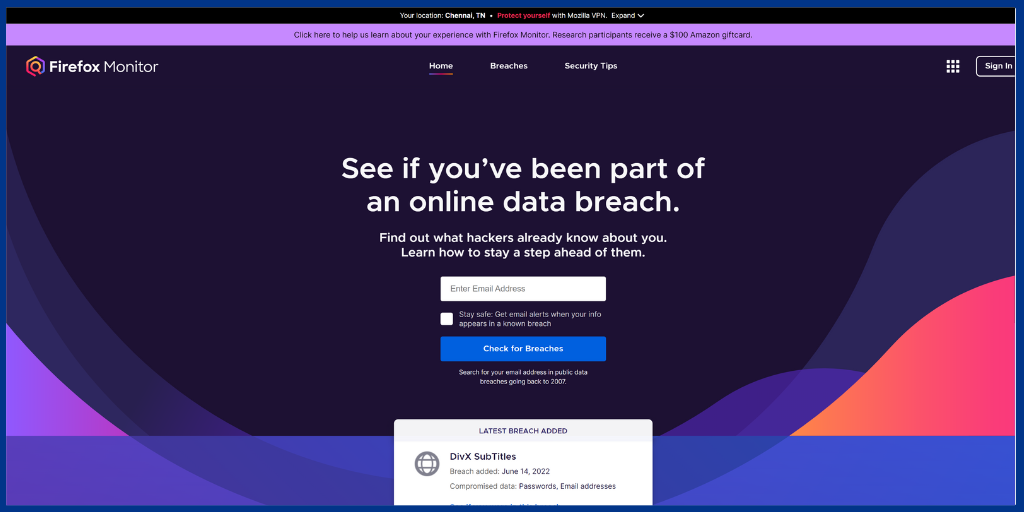
Firefox Monitor is an effective and efficient security tool that alerts you if your used email has been hacked.
The platform uses a sensible method to decide whether your data is at risk or not, and if it is, the system will quickly warn you if a new data breach occurs.
Based on your personal details to your data, Firefox Monitor gives current and historical breach reports.
With conditional choices, Firefox gives you options for how to protect your data from thieves.
Also, this software helps consumers restore control by providing deeper insights into the leaks.
Like many of the software programs created by the company, this product features a clear and user-friendly interface that makes it simple to use even for beginners.
#5 Leakwatch
Leakwatch is a great tool for anyone who wants to make sure their information is safe online.
Users can check for any data and information leaks by Java programs they are utilizing using this Java API and command-line tool, which is flexible.
To put it in simple terms, this platform is popular with users because the chances of high false notifications are reduced.
Users will receive a notification if any of their personal information is hacked.
Another key advantage of the platform, besides the absence of installation requirements, is the availability of free membership as well as its ease of use.
Additionally, it gives you the ability to build up a central platform to keep track of any systemic data breaches.
#6 Spybot Identity Monitor
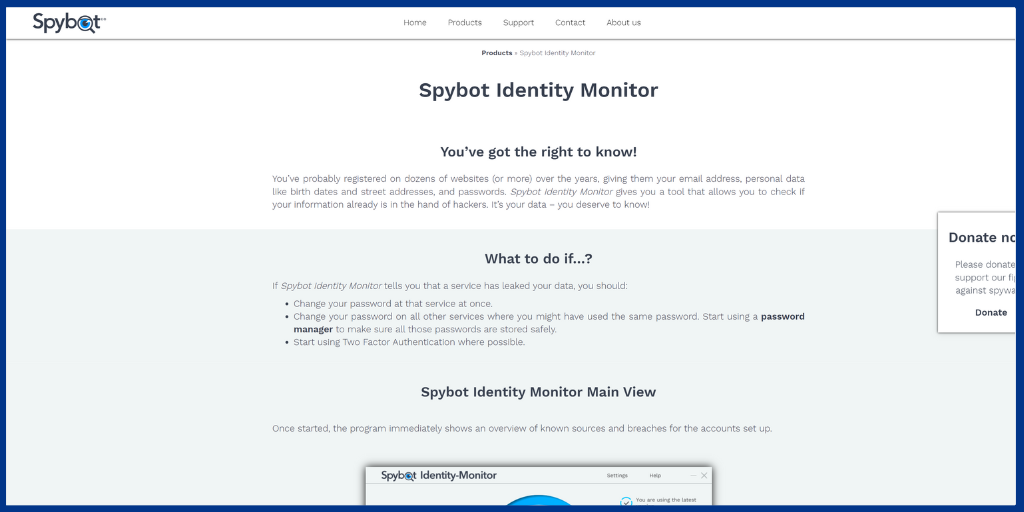
Spybot Identity Monitor is a flexible threat detection program that gives you tools to determine whether or not a hacker has access to your information.
Also, it notifies you immediately if your data or personal information has been taken.
So if you notice anything you can change your password.
You only need to enter your email address to view all the facts about the data breach, and the program is easy to install and use.
All of your emails will be included, and you are free to add as many accounts as you like.
Users can get a summary of breaches and known sources for the set of an account using Spybot Identity Monitor’s alerting service.
#7 Mypwd
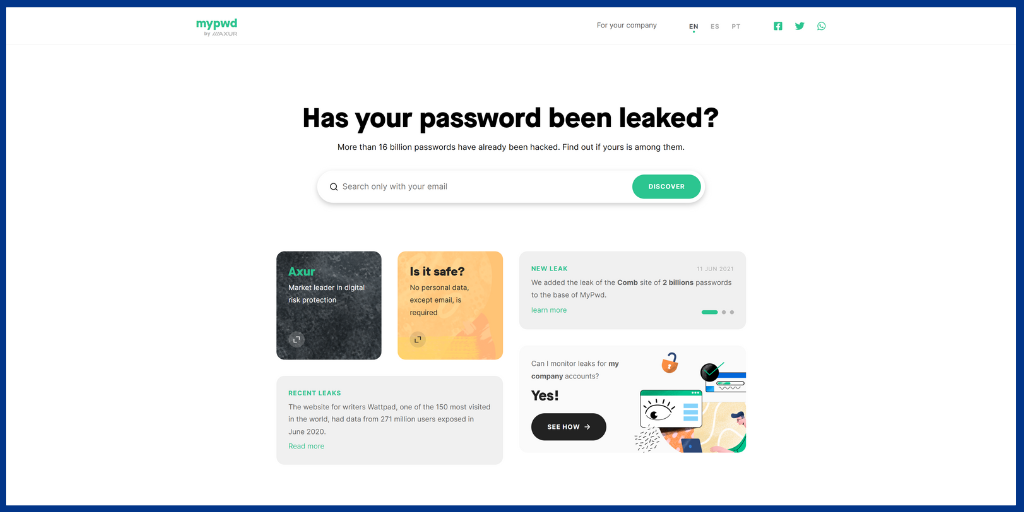
MyPwd is an advanced platform that makes it easier for you to locate the email and password that have been hacked.
The software uses a systematic strategy to take the essential steps when your website, passwords, or usernames are hacked.
There have been over nine billion data leaks according to MyPwd. However, they also provide more detailed information about available leaks.
Also, the platform is doing a great job addressing cybercriminals involved in a variety of crimes, including bank fraud, the manipulation of personal information, crimes committed in chat applications, and more.
MyPwd uses amazing artificial intelligence that makes it easy to browse the deep web and the black web.
#8 We Leak Info
We Leak Info is a website that provides its users with services for data breaches.
More than eight billion entries are accessible to users through the site, and the database is constantly updated.
People can search for and discover leaked material due to the platform’s connection with various programs and websites.
It enables users to look up usernames, emails, passwords, IP addresses, phone numbers, domain names, etc
Users can also use regex and wildcard searching to gain more details on leaks.
#9 Inoitsu
Inoitsu is a platform that enables users to examine their email in order to determine whether it has been hacked or not.
Users of the platform can enter their email addresses in the search field and submit the form by clicking the submit button.
So the user can quickly identify whether their email address has been hacked or not.
In order to know the status of their addresses, users can also receive updates on all the findings acquired by various other platforms.
Finally, it helps in the understanding of the detection of user data fraud and theft.
This is also one of the best Dehashed Alternatives.
#10 Have I been pwned?
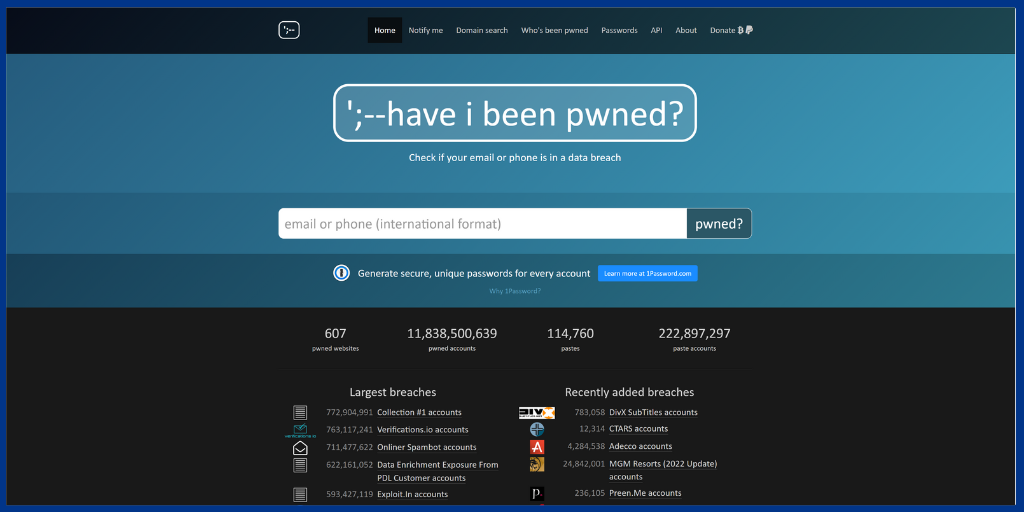
Have I been pwned? is a tool that lets users determine whether their personal data has been hacked or not.
Since users can only use an email address or phone number to query their databases, the platform does not support a wide range of search criteria.
Additionally, it uses a special password to protect access to the user’s data and emails while searching the results.
Users of the platform can get information on how many websites and email accounts have had their data compromised so far.
Further, they can look up verified accounts and check the status of accounts across other sites.
Conclusion:
So these are the 10 Dehashed Alternatives. Leakcheck is the platform that I’d recommend because it’s safe and also helps businesses and developers to keep their data. Hope you find this blog helpful and if it is so share it with your friends.
Follow Publish Square for more blogs like this.